代码工程的GITHUB连接:
https://github.com/sj15712795029/stm32f1_marvell88w8801_marvell8801_wifi
1.Linux SDIO WIFI Marvell8801/Marvell88w8801(一) — 代码及文档介绍
2. Linux SDIO WIFI Marvell8801/Marvell88w8801(二) — Marvell88w8801驱动编译
3. Linux SDIO WIFI Marvell8801/Marvell88w8801(三) — Linux驱动以及组件的使用
4. Linux SDIO WIFI Marvell8801/Marvell88w8801(四) — Linux Wi-Fi架构
5. Linux SDIO WIFI Marvell8801/Marvell88w8801(五) — Linux SDIO API介绍
6. Linux SDIO WIFI Marvell8801/Marvell88w8801(六) — Marvell Linux Wi-Fi driver介绍-WIFI插入卡槽内发生的事情
7. Linux SDIO WIFI Marvell8801/Marvell88w8801(七) — Marvell Linux Wi-Fi driver初始化
8. Linux SDIO WIFI Marvell8801/Marvell88w8801(八) — Marvell Linux Wi-Fi driver 对接芯片上行下行接口介绍
关于Linux驱动以及组件的使用介绍主要分为以下图示几部分介绍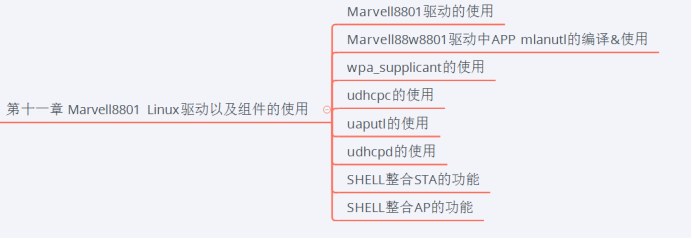
1)Marvell8801驱动使用,主要扩展介绍驱动的加载以及使用
2)Marvell驱动中APP mlanutl的编译使用,主要对marvell官方自带的验证驱动的app做编译使用说明
3)wpa_supplicant的使用介绍
4)Udhcpc的使用,由于wpa_supplicant只能连接热点,不能主动向AP索要IP,此APP就是DHCP client
5)Marvell驱动中APP uaptul的编译使用
6)Udhcpd的使用,主要是DHCP server的使用
7)SHELL整合STA的功能
8)SHELL整合AP的功能
在上一篇文章我们加载驱动方式只是用了:
insmod ./mlan.ko
insmod ./sd8xxx.ko
这种方法一下就是把STA,AP,WIFIDIRECT mode的interface都做出来,但是如果我们想要其中的某一个interface,那么看下面就对了
1)首先模式加载可以选择,参数是drv_mode,默认是STA,UAP,WIFIDIRECT都有,所以有3个节点:mlan0,uap0,wfd0,这个driver mode的值见下面
The bit settings of drv_mode are,
Bit 0 : STA
Bit 1 : uAP
Bit 2 : WIFIDIRECT
The default drv_mode is 7.
举一个例子:
insmod mlan.ko
insmod sd8xxx.ko drv_mode=1
这样就是只设置了STA mode,这样设置后就会发现只会有mlan0出现
其他参数如下,你们可以自己试下其他的:
max_sta_bss: Maximum number of STA BSS (default 1, max 1)
sta_name: Name of the STA interface (default: “mlan”)
max_uap_bss: Maximum number of uAP BSS (default 1, max 2)
uap_name: Name of the uAP interface (default: “uap”)
max_wfd_bss: Maximum number of WIFIDIRECT BSS (default 1, max 1)
wfd_name: Name of the WIFIDIRECT interface (default: “wfd”)
2)运行时切换状态
echo drv_mode=1 > /proc/mwlan/config // STA mode
echo drv_mode=2 > /proc/mwlan/config // uAP mode
echo drv_mode=3 > /proc/mwlan/config // STA uAP mode
echo drv_mode=7 > /proc/mwlan/config // STA uAP WIFIDIRECT mode
1)加载完毕驱动在 /proc/mwlan中会发现3个文件夹和一个文件,分别是mlan0,uap0,wfd0,config文件
不过文件夹要看你选择什么模式加载,如果你选择drv_mode 7就是三个
The following info are provided in /proc/net/mwlan/mlanX|uapX|wfdX/info,
on kernel 2.6.24 or later, the entry is /proc/mwlan/mlanX|uapX|wfdX/info.
此部分可以查看一些基本信息,你可以自动去看下,对我来说也就是扫一眼,对我来说没有太大的作用,但是还是要列出来,万一有想到想知道一个信息,直接先通过这里查看有没有
driver_name = “wlan” or “uap”
driver_version = <chip id, firmware version and driver version>
interface_name = “mlanX”, “uapX” or “wfdX”
bss_mode = “Ad-hoc” | “Managed” | “Auto” | “Unknown”
media_state = “Disconnected” | “Connected”
mac_address = <6-byte adapter MAC address>
multicase_count = // Only for STA
essid = // Only for STA
bssid = // Only for STA
channel = // Only for STA
region_code = // Only for STA
multicast_address[n] = // Only for STA
num_tx_bytes =
num_rx_bytes =
num_tx_pkts =
num_rx_pkts =
num_tx_pkts_dropped =
num_rx_pkts_dropped =
num_tx_pkts_err =
num_rx_pkts_err =
carrier “on” | “off”
tx queue “stopped” | “started”
tkip_mic_failures = 0 // Only for uAP
ccmp_decrypt_errors = 0 // Only for uAP
wep_undecryptable_count = 0 // Only for uAP
wep_icv_error_count = 0 // Only for uAP
decrypt_failure_count = 0 // Only for uAP
mcast_tx_count = 0 // Only for uAP
failed_count = 0 // Only for uAP
retry_count = 0 // Only for uAP
multiple_retry_count = 0 // Only for uAP
frame_duplicate_count = 0 // Only for uAP
rts_success_count = 0 // Only for uAP
rts_failure_count = 0 // Only for uAP
ack_failure_count = 0 // Only for uAP
rx_fragment_count = 0 // Only for uAP
mcast_rx_frame_count = 0 // Only for uAP
fcs_error_count = 0 // Only for uAP
tx_frame_count = 0 // Only for uAP
rsna_tkip_cm_invoked = 0 // Only for uAP
rsna_4way_hshk_failures = 0 // Only for uAP
The following debug info are provided in /proc/net/mwlan/mlanX|uapX|wfdX/debug,
on kernel 2.6.24 or later, the entry is /proc/mwlan/mlanX|uapX|wfdX/debug.
此部分可以纵览一些运行情况,也就是debug信息,或者说是统计情况
drvdbg =
wmm_ac_vo =
wmm_ac_vi =
wmm_ac_be =
wmm_ac_bk =
max_tx_buf_size =
tx_buf_size =
curr_tx_buf_size =
ps_mode = <0/1, CAM mode/PS mode>
ps_state = <0/1/2/3, awake state/pre-sleep state/sleep-confirm state/sleep state>
is_deep_sleep = <0/1, not deep sleep state/deep sleep state> // Only for STA
wakeup_dev_req = <0/1, wakeup device not required/required>
wakeup_tries = <wakeup device count, cleared when device awake>
hs_configured = <0/1, host sleep not configured/configured>
hs_activated = <0/1, extended host sleep not activated/activated>
tx_pkts_queued =
pps_uapsd_mode = <0/1, PPS/UAPSD mode disabled/enabled> // Only for STA
sleep_pd = // Only for STA
qos_cfg = // Only for STA
tx_lock_flag = <0/1, Tx lock flag> // Only for STA
port_open = <0/1, port open flag> // Only for STA
scan_processing = <0/1, scan processing flag> // Only for STA
num_bridge_pkts = // Only for uAP
num_drop_pkts = // Only for uAP
num_tx_timeout =
num_cmd_timeout =
timeout_cmd_id =
timeout_cmd_act =
last_cmd_id =
last_cmd_act =
last_cmd_index = <0 based last command index>
last_cmd_resp_id =
last_cmd_resp_index = <0 based last command response index>
last_event =
last_event_index = <0 based last event index>
num_cmd_h2c_fail =
num_cmd_sleep_cfm_fail =
num_tx_h2c_fail =
num_cmdevt_c2h_fail = <number of commands/events failed to receive from device>
num_rx_c2h_fail =
num_int_read_fail =
last_int_status =
num_evt_deauth = // Only for STA
num_evt_disassoc = // Only for STA
num_evt_link_lost = // Only for STA
num_cmd_deauth = // Only for STA
num_cmd_assoc_ok = // Only for STA
num_cmd_assoc_fail = // Only for STA
cmd_sent = <0/1, send command resources available/sending command to device>
data_sent = <0/1, send data resources available/sending data to device>
mp_rd_bitmap =
curr_rd_port =
mp_wr_bitmap =
curr_wr_port =
cmd_resp_received = <0/1, no cmd response to process/response received and yet to process>
event_received = <0/1, no event to process/event received and yet to process>
ioctl_pending =
tx_pending =
rx_pending =
lock_count =
malloc_count =
mbufalloc_count =
main_state =
sdiocmd53w =
sdiocmd53r =
hs_skip_count =
hs_force_count =
此部分是用于调试Wi-FI寄存器的,也就是直接通过CMD52修改获取读出来寄存器的值
Issue SDIO cmd52 read/write through proc.Usage:
echo “sdcmd52rw= [data]” > /proc/mwlan/config
where the parameters:
func: The function number to use (0-7)
reg: The address of the register
data: The value to write, read if the value is absent
For SDIO MMC driver, only function 0 and WLAN function access is allowed.
And there is a limitation for function 0 write, only vendor specific CCCR
registers (0xf0 -0xff) are permiited.
Examples:
echo “sdcmd52rw= 0 4” > /proc/mwlan/config # read func 0 address 4
cat /proc/mwlan/config # display the register value
echo “sdcmd52rw= 1 3 0xf” > /proc/mwlan/config# write 0xf to func 1 address 3
read会跳出read value (0x2) from func 0 reg 0x4
分为几个步骤:
1)修改mapp/mlanutl下的makefile
增加CC = arm-linux-gcc
2)在wlan_src下敲指令
make mapp/mlanutl
做完以上两步就会提到mlanutl
1)help指令
./mlanutl --help
会得到运行的格式:mlanutl […]
其中ifname:wireless network interface name, such as mlanX or uapX,我们是用的mlanutl,所以我们这部分填写mlan0,cmd list自己敲下命令,有很多,我就不列举,我只是会说明一些常用的指令
2)assocessid
人家文档中说的很详细了,我就不做累赘
This command is used to assoc essid with asynced mode,and driver will auto retry if driver auto assoc enabled.
Usage:
mlanutl mlanX assocessid <"[essid]">
Where
<"[essid]"> is the essid which need to be associated with asynced mode.
Examples:
mlanutl mlan0 assocessid “Marvell Micro AP”
使用:连接一个open的ssid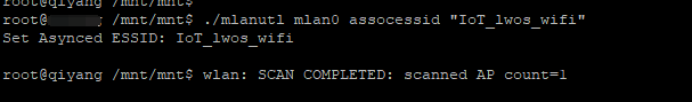
获取一下刚刚的proc的信息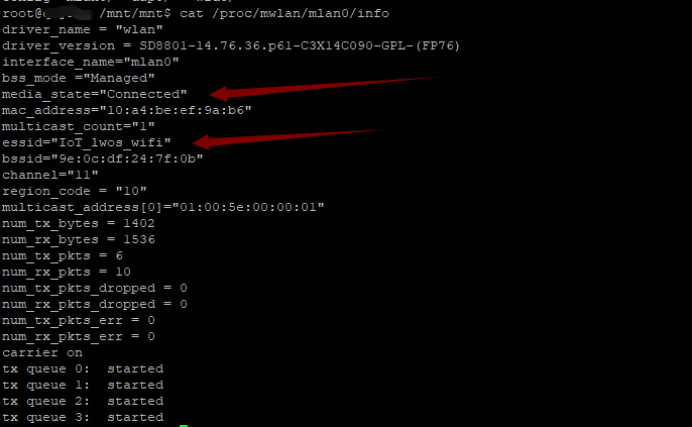
分配IP并且ping,其实此部分可以通过udhcpc,但是用法后面再说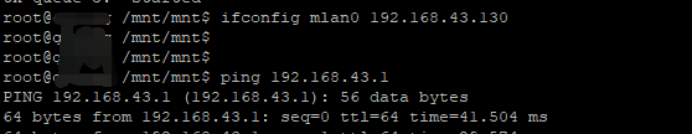
3)Deauth
从热点断线,执行下面命令就断线了
./mlanutl mlan0 deauth
4)Scan
Scan的介绍还是比较多的,我给你说下最简单的应用,详细还是要你们自己看下
执行在termainal上敲命令:./mlanutl mlan0 setuserscan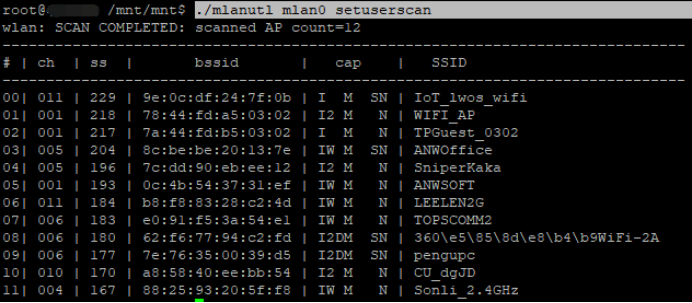
以上是介绍了Marvell Linux wifi驱动的APP测试工具,那么现在我们也试着用下wpa_supplicant的工具,毕竟此工具比较通用,以后大部分的wifi驱动是可以用这个工具实现STA mode的加密认证的。
先从readme中看看是否有找到一些重要的信息
Wpa_supplicant一共生成三个工具:wpa_cli,wpa_supplicant,wpa_passphrase
主要介绍下前两个:
1)usage:
wpa_supplicant [-BddfhKLqqtuvwW] [-P] [-g]
-i -c [-C] [-D] [-p<driver_param>]
[-b<br_ifname> [-N -i -c [-C] [-D]
[-p<driver_param>] [-b<br_ifname>] …]
options:
-b = optional bridge interface name
-B = run daemon in the background
-c = Configuration file
-C = ctrl_interface parameter (only used if -c is not)
-i = interface name
-d = increase debugging verbosity (-dd even more)
-D = driver name (can be multiple drivers: nl80211,wext)
-f = Log output to default log location (normally /tmp)
-g = global ctrl_interface
-K = include keys (passwords, etc.) in debug output
-t = include timestamp in debug messages
-h = show this help text
-L = show license (BSD)
-p = driver parameters
-P = PID file
-q = decrease debugging verbosity (-qq even less)
-u = enable DBus control interface
-v = show version
-w = wait for interface to be added, if needed
-W = wait for a control interface monitor before starting
-N = start describing new interface
看完这个,我们大概已经知道有用法的概念了
wpa_supplicant -B -cxxx.conf -iwlan0
2)配置文件,我们直接列出配置文件,然后再一个个验证
没有加密的配置文件
ctrl_interface=/var/run/wpa_supplicant
network={
ssid=“IoT_lwos_wifi”
key_mgmt=NONE
}
WEP的配置文件
ctrl_interface=/var/run/wpa_supplicant
network={
ssid=“IoT_lwos_wifi”
key_mgmt=NONE
wep_key0=“IoT_lwos_wifi”
wep_tx_keyidx=0
}
WPA的配置文件
ctrl_interface=/var/run/wpa_supplicant
network={
ssid=“IoT_lwos_wifi”
proto=WPA # proto: list of accepted protocols, 可取WPA,RSN
# If not set, this defaults to: WPA RSN
key_mgmt=WPA-PSK # 认证方式
# If not set, this defaults to: WPA-PSK WPA-EAP
pairwise=TKIP # If not set, this defaults to: CCMP TKIP
group=TKIP # If not set, this defaults to: CCMP TKIP WEP104 WEP40
psk=“12345678”
}
WPA2的配置文件
ctrl_interface=/var/run/wpa_supplicant
network={
ssid=“IoT_lwos_wifi”
psk=“12345678”
}
那么我们就一个个的验证:
Open方式的验证
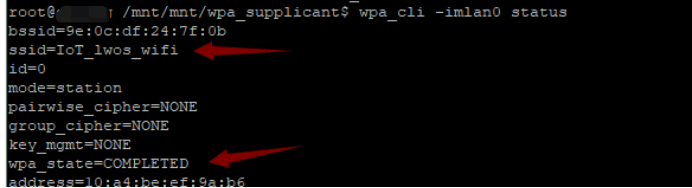
wpa_supplicant -B -cxxx.conf -iwlan0
wpa_cli -iwlan0 status // 查看状态
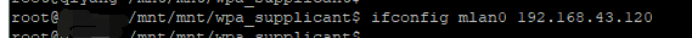
ifconfig wlan0 192.168.43.120
ping 192.168.43.120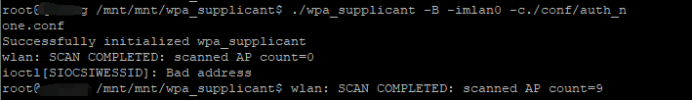
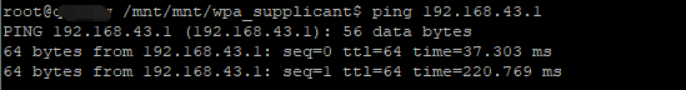
其他的加密方式验证方法以及命令都一样,所以不再累赘
wpa_cli commands
status = get current WPA/EAPOL/EAP status
mib = get MIB variables (dot1x, dot11)
help = show this usage help
interface [ifname] = show interfaces/select interface
level = change debug level
license = show full wpa_cli license
logoff = IEEE 802.1X EAPOL state machine logoff
logon = IEEE 802.1X EAPOL state machine logon
set = set variables (shows list of variables when run without arguments)
pmksa = show PMKSA cache
reassociate = force reassociation
reconfigure = force wpa_supplicant to re-read its configuration file
preauthenticate = force preauthentication
identity = configure identity for an SSID
password = configure password for an SSID
pin = configure pin for an SSID
otp = configure one-time-password for an SSID
passphrase = configure private key passphrase
for an SSID
bssid = set preferred BSSID for an SSID
list_networks = list configured networks
select_network = select a network (disable others)
enable_network = enable a network
disable_network = disable a network
add_network = add a network
remove_network = remove a network
set_network = set network variables (shows
list of variables when run without arguments)
get_network = get network variables
save_config = save the current configuration
disconnect = disconnect and wait for reassociate command before connecting
scan = request new BSS scan
scan_results = get latest scan results
get_capability <eap/pairwise/group/key_mgmt/proto/auth_alg> = get capabilies
terminate = terminate wpa_supplicant
quit = exit wpa_cli
Wpa_cli分为两种模式:
1)交互模式,输入wap_cli按回车健就能进入,然后可以随便输入以上命令,输去quit退出
2)命令行模式,就是在terminal上敲命令,格式如下
wpa_cli command line options
wpa_cli [-p
[-P] [-g] [command…]
-h = help (show this usage text)
-v = shown version information
-a = run in daemon mode executing the action file based on events from
wpa_supplicant
-B = run a daemon in the background
default path: /var/run/wpa_supplicant
default interface: first interface found in socket path
下面我们直接用交互模式说明一些常用的命令,其实和命令是一样的道理
1)搜索:scan
scan_result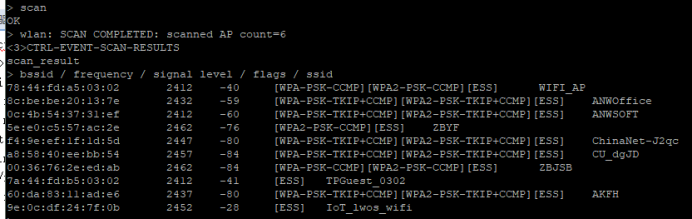
3)连接无密码网络
注意一下有几点需要注意的点:
1)index id不是写死的,是根据add_network返回的值
2)连接不成功很有可能是因为中英文输入法造成,我开始在这里耗费了半个小时怎么都连接不成功,返现敲的命令没错,但是实际是错的,有乱码行为,怎么知道敲的是否对呢,这样,拿ssid为例,你可以敲 get_network 1 ssid看返回
add_network
set_network 1 ssid “IoT_lwos_wifi”
set_network 1 key_mgmt NONE
select_network 1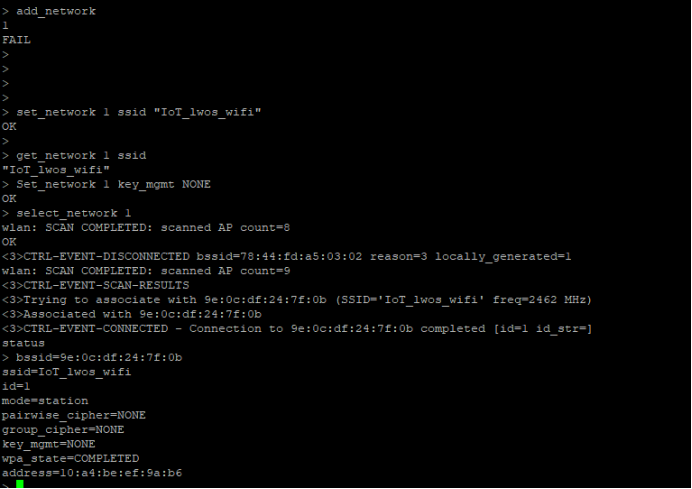
4)在连接回来WPA2的模式
add_network
set_network 2 ssid “WIFI_AP”
set_network 2 key_mgmt WPA-PSK
set_network 2 psk “12345678”
select_network 2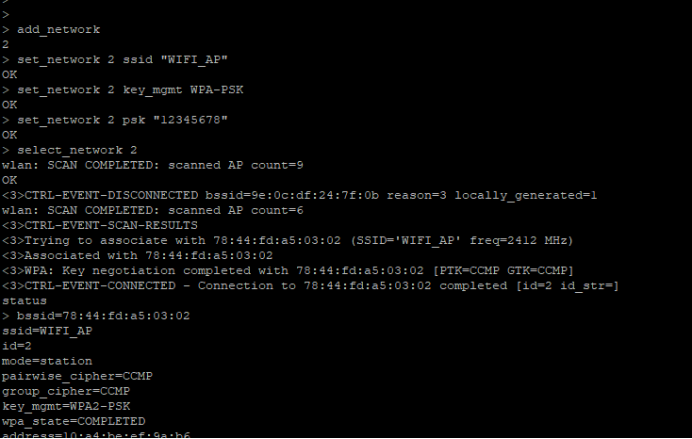
这个文章的逻辑很缜密啊,你觉得哪里不合理那么就会出现什么,哈哈,自己夸自己也是没谁了,为什么说上面不太合理呢,因为你没发现连接上,以后就没有然后了,IP呢?只能手动分配,敲ifconfig命令(PS:也许有的手机你曾经敲过ifconfig后还是给你保留原IP),那么既然有上面的不合理我们就解决他,通过dhcp client的角色自动向dhcp server索要IP。
怎样编译已经在上篇文章说明了,再这里就不再提,只是说怎样使用,命令行格式如下
-c, --clientid=CLIENTID Client identifier
-H, --hostname=HOSTNAME Client hostname
-h, Alias for -H
-f, --foreground Do not fork after getting lease
-b, --background Fork to background if lease cannot be immediately negotiated.
-i, --interface=INTERFACE Interface to use (default: eth0)
-n, --now Exit with failure if lease cannot be immediately negotiated.
-p, --pidfile=file Store process ID of daemon in file
-q, --quit Quit after obtaining lease
-r, --request=IP IP address to request (default: none)
-s, --script=file Run file at dhcp events (default:
/usr/share/udhcpc/default.script)
-v, --version Display version
这样我们就知道大概用法了 udhcpc -imlan0
首先用之前我们先看下网卡的状态以及是否有IP地址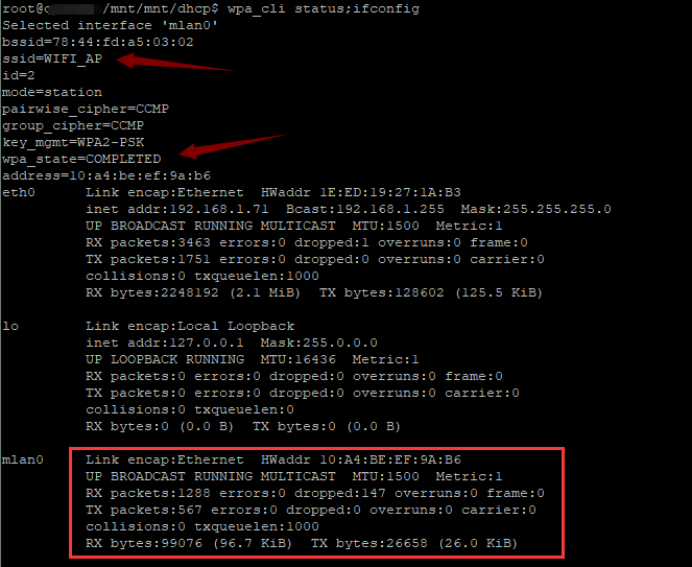
执行完毕后我们发现变成了这样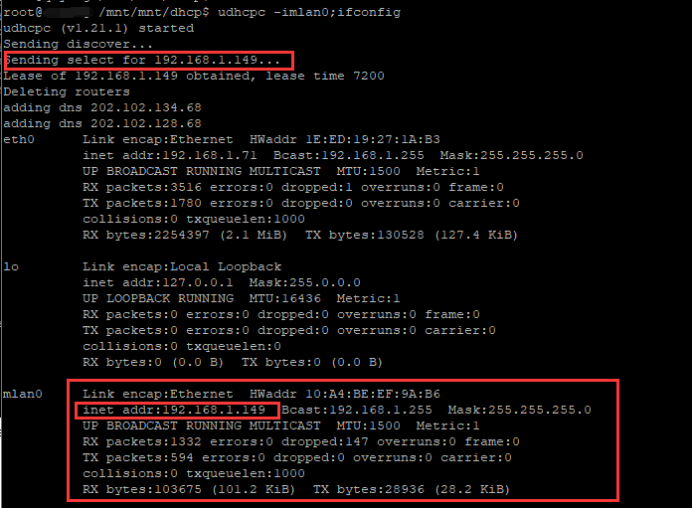
Udhcpc的使用还是比较简单的
啊,惭愧啊,接着上篇,还是没有用起来hostapd,所以用这个uaputl替代吧
分为几个步骤:
1)修改mapp/uaputl下的makefile
增加CC = arm-linux-gcc
2)在wlan_src下敲指令
make make mapp/uaputl
做完以上两步就会提到uaputl.exe
看功能还是直接看readme比较官方
格式为:
uaputl.exe [options] [command parameters]]
Options:
–help Display help
-v Display version
-i
-d <debug_level=0|1|2>
Example:
./uaputl.exe --help
“display help for uaputl”
./uaputl.exe sys_config --help
"display help for sys_config command"
This tool can be used to set/get uAP’s settings. To change AP settings, you might
need to issue “bss_stop” command to stop AP before making change and issue “bss_start”
command to restart the AP after making change.
version
debug_level
sys_config [CONFIG_FILE_NAME]
bss_config [CONFIG_FILE_NAME]
sys_info
sys_reset
bss_start
bss_stop
sta_list
sta_deauth <STA_MAC_ADDRESS>
sta_deauth_ext <STA_MAC_ADDRESS> <REASON_CODE>
radioctrl [0|1]
txratecfg [l] [m] [n]
pscfg [MODE] [CTRL INACTTO MIN_SLEEP MAX_SLEEP MIN_AWAKE MAX_AWAKE]
sys_cfg_custom_ie [INDEX] [MASK] [IEBuffer]
hscfg [condition [[GPIO# [gap]]]]
hssetpara condition [[GPIO# [gap]]]
sys_cfg_wmm [qosinfo=]
[AC_BE AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_BK AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_VI AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_VO AIFSN ECW_MAX ECW_MIN TX_OP]
sys_cfg_ap_wmm [0]
[AC_BE AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_BK AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_VI AIFSN ECW_MAX ECW_MIN TX_OP]
[AC_VO AIFSN ECW_MAX ECW_MIN TX_OP]
sys_cfg_11n [ENABLE] [HTCAP] [AMPDU] [TXBFCAP] [HT_MCS_MAP]
addbapara [timeout txwinsize rxwinsize txamsdu rxamsdu]
aggrpriotbl …
addbareject …
httxcfg [] []
deepsleep [MODE] [IDLE_TIME]
sdcmd52rw
sys_cfg_ap_mac_address [AP_MAC_ADDRESS]
sys_cfg_ssid [SSID]
sys_cfg_beacon_period [BEACON_PERIOD]
sys_cfg_dtim_period [DTIM_PERIOD]
sys_cfg_channel [CHANNEL] [MODE]
sys_cfg_scan_channels [CHANNEL[.BAND]]
sys_cfg_rates [RATES]
sys_cfg_rates_ext [rates RATES] [mbrate RATE]
sys_cfg_tx_power [TX_POWER]
sys_cfg_bcast_ssid_ctl [1|0]
sys_cfg_preamble_ctl
sys_cfg_bss_status
sys_cfg_antenna_ctl [MODE]
sys_cfg_rts_threshold [RTS_THRESHOLD]
sys_cfg_frag_threshold [FRAG_THRESHOLD]
sys_cfg_rsn_replay_prot [1|0]
sys_cfg_mcbc_data_rate [MCBC_DATA_RATE]
sys_cfg_pkt_fwd_ctl [PKT_FWD_CTRL]
sys_cfg_sta_ageout_timer [STA_AGEOUT_TIMER]
sys_cfg_ps_sta_ageout_timer [PS_STA_AGEOUT_TIMER]
sys_cfg_auth [AUTH_MODE]
sys_cfg_protocol [PROTOCOL] [AKM_SUITE]
sys_cfg_pmf [MFPC] [MFPR]
sys_cfg_wep_key [INDEX ISDEFAULT KEY]
sys_cfg_cipher [PAIRWISE_CIPHER GROUP_CIPHER]
sys_cfg_pwk_cipher [] [PAIRWISE_CIPHER]
sys_cfg_gwk_cipher [GROUP_CIPHER]
sys_cfg_group_rekey_timer [GROUP_REKEY_TIMER]
sys_cfg_wpa_passphrase [PASSPHRASE]
sys_cfg_max_sta_num [STA_NUM]
sys_cfg_retry_limit [RETRY_LIMIT]
sys_cfg_sticky_tim_config [ENABLE] [ <STICKY_BIT_MASK>]
sys_cfg_sticky_tim_sta_mac_addr [CONTROL] [STA_MAC_ADDRESS]
sys_cfg_2040_coex [ENABLE]
sys_cfg_eapol_pwk_hsk [ ]
sys_cfg_eapol_gwk_hsk [ ]
sta_filter_table <MACADDRESS_LIST>
regrdwr [value]
memaccess [value]
rdeeprom
cfg_data [*.conf]
sys_cfg_80211d [state STATE] [country COUNTRY]
uap_stats
sys_cfg_restrict_client_mode [ [MODE_CONFIG]]
又是一大堆啊·,那么还是老样子,常规功能使用
友情提示几点:自带的conf文件MaxStaNum为10,但是如果按照自带的conf文件使用,会报最大的sta的个数不能超过8个的错误
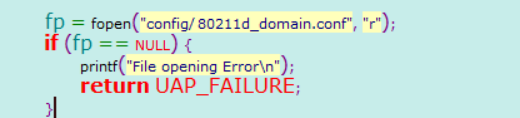
另外一个需要注意的点是:我开始用bss_start一直报错,后来查看代码发现需要把uaputl的conf文件夹一起拿过去,这个是通过查看代码得知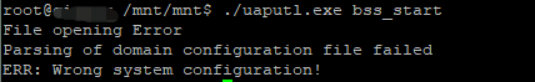
先来创建个热点玩玩:
分为几点:
5.2.1 创建一个没有密码的热点
步骤:
修改配置配置文件(配置文件太多,就不都列出来)
SSID=“IoT_lwos_wifi_none”
MaxStaNum=6
敲命令
./uaputl.exe bss_config ./config/uaputl_none.conf
./uaputl.exe bss_start
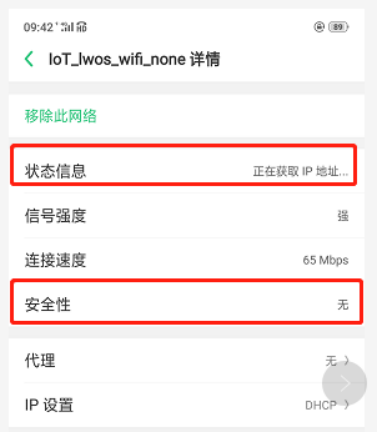
结果,会有类似log提示,并且手机提示正在获取IP,代表连接成功,但是分配不到IP,因为我们没弄dhcp server的部分,肯定是分配不到IP了,下一part讲dhcpd的部分。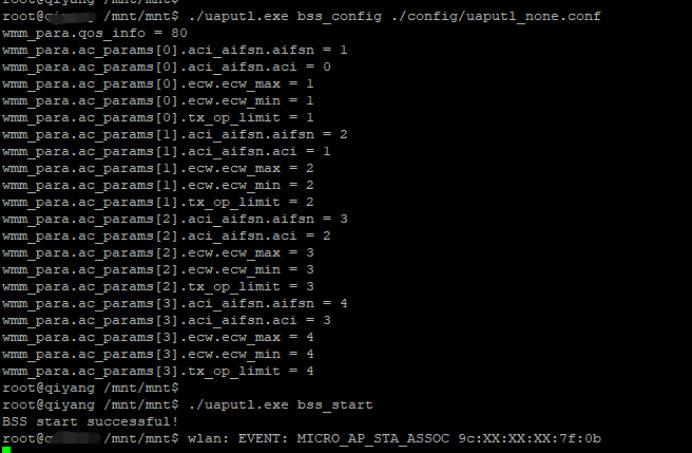
5.2.2创建一个WPA的热点
步骤:
PS:在开始一个新的热点之前,需要敲bss_stop指令
1)修改配置配置文件(配置文件太多,就不都列出来)
SSID=“IoT_lwos_wifi_wpa”
MaxStaNum=6
Protocol=8
PwkCipherWPA=12
GwkCipher=4
PSK=“12345678”
2)敲命令
./uaputl.exe bss_config ./config/uaputl_wpa.conf
./uaputl.exe bss_start
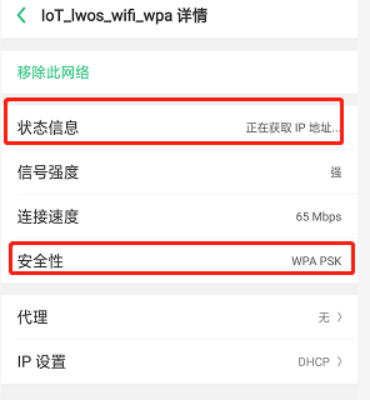
3)结果,会有类似log提示,并且手机提示正在获取IP,代表连接成功,但是分配不到IP,因为我们没弄dhcp server的部分,肯定是分配不到IP了,下一part讲dhcpd的部分。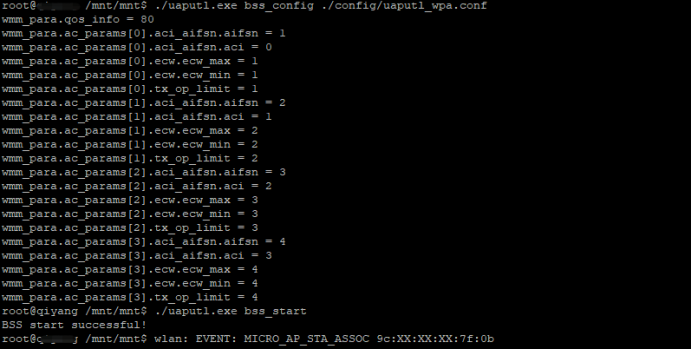
步骤:
PS:在开始一个新的热点之前,需要敲bss_stop指令
1)修改配置配置文件(配置文件太多,就不都列出来)
SSID=“IoT_lwos_wifi_wpa2”
MaxStaNum=6
Protocol=32
PwkCipherWPA2=8
GwkCipher=8
PSK=“12345678”
2)敲命令
./uaputl.exe bss_config ./config/uaputl_wpa2.conf
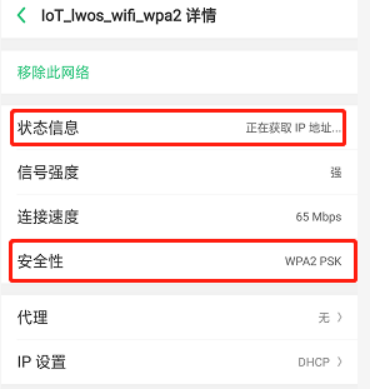
./uaputl.exe bss_start
3)结果,会有类似log提示,并且手机提示正在获取IP,代表连接成功,但是分配不到IP,因为我们没弄dhcp server的部分,肯定是分配不到IP了,下一part讲dhcpd的部分。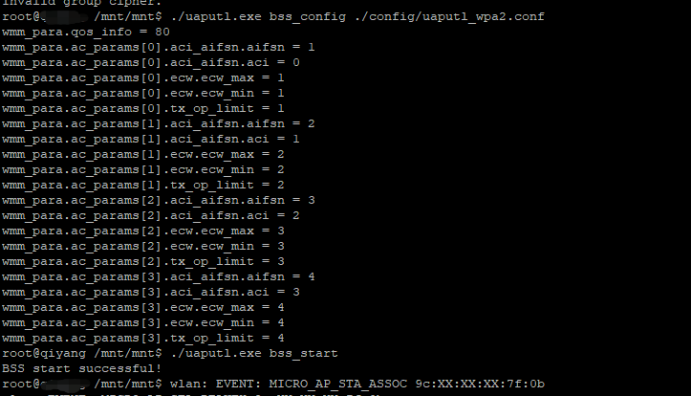
udhcpd的使用很简单,步骤如下:
1)修改udhcpd 配置文件
我们可以看到默认的已经自带了配置文件,所以我们大致修改下配置文件,修改完的配置文件见连接:xxxx
修改如下:
start 192.168.10.100
end 192.168.10.254
interface uap0
2)创建一个文件/var/lib/misc/udhcpd.leases
3)ifconfig uap0 up;ifconfig uap0 192.168.1.1 启动网卡并且分配AP的IP地址
4)启动dhcpd
./udhcpd ./udhcpd.conf
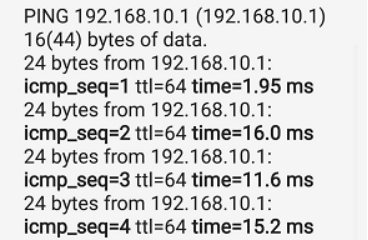
5)然后用手机连接并且PING一下看看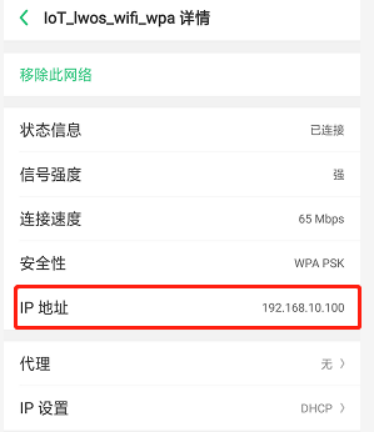
啊,爽了···所有的功能都已经完成了,但是你没发现我们开机要敲一堆命令很烦人吗?我们要不要搞一个shell来玩玩,开机敲一下,所以的动作都帮我完成,说搞咱就搞
此部分没啥好特别说明的,就是把之前的命令用shell整合到一起,不再逐条敲,那我就直接贴出来shell供大家参考,仅供参考,因为每个人的路径不同
#!/bin/bash
insmod /lib/firmware/mrvl/mlan.ko
insmod /lib/firmware/mrvl/sd8xxx.ko
cd /mnt/mnt/
cd wpa_supplicant/
wpa_supplicant -B -c./conf/auth_wpa.conf -imlan0
sleep 2
cd …/dhcp/
./udhcpc -imlan0
#!/bin/bash
insmod /lib/firmware/mrvl/mlan.ko
insmod /lib/firmware/mrvl/sd8xxx.ko
cd /mnt/mnt/
./mlanutl mlan0 assocessid “IoT_lwos_wifi”
cd ./dhcp/
./udhcpc -imlan0
此部分同样没啥好特别说明的,就是把之前的命令用shell整合到一起,不再逐条敲,那我就直接贴出来shell供大家参考,仅供参考,因为每个人的路径不同
#!/bin/bash
insmod /lib/firmware/mrvl/mlan.ko
insmod /lib/firmware/mrvl/sd8xxx.ko
cd /mnt/mnt/
./uaputl.exe bss_config ./config/uaputl_wpa2.conf
./uaputl.exe bss_start
cd ./dhcp/
mkdir /var/lib/misc
touch /var/lib/misc/udhcpd.leases
ifconfig uap0 up
ifconfig uap0 192.168.10.1
./udhcpd ./udhcpd.conf